Police use numerous methods to access your locked smartphone
The single most valuable new police tool is your smartphone.
Rolf Norton, a homicide detective in Seattle, says when he's talking to a suspect, he keeps his eye open for the person's smartphone.
"I'm thinking there's probably a wealth of information that just got tucked into your pocket," Norton says. "Something that we'd like to get our hands on."
Your calls, your emails, your calendar, your photos — not to mention the GPS data embedded in those photos — could make a whole case, in one convenient package.
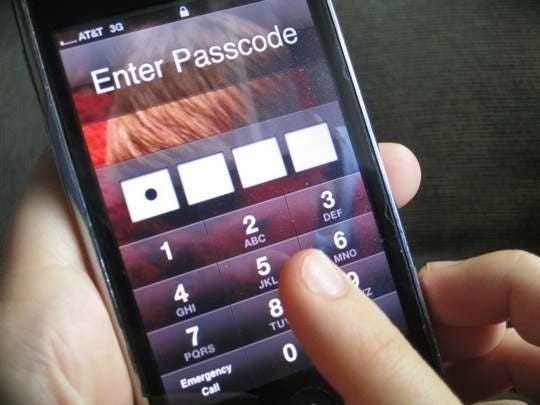
That wealth of information is also why more people now keep their phones locked with a PIN. Once he's seized a phone, Norton says, he often has to return to the owner to ask for help.
"Maybe you've established a rapport and you're getting along with this person," Norton says. "We'll reach out to that person and say, 'Hey, your phone's locked. We'd like to inspect it. We'll probably be getting a warrant. Would you give us your password?' "
Under the Fifth Amendment's protection against self-incrimination, you might have the right to refuse. But Jeffrey Fisher, a Stanford Law School professor, says the courts haven't settled that issue, so withholding your phone's password could prove risky.
"You can have anything from contempt of court to obstruction of justice," Fisher says. "All kinds of other problems."
Plus, there's a practical consideration: The police may be able to get around your password, anyway.
Companies such as Guidance Software and Cellebrite sell products to law enforcement that "image" smartphones. The products can pull data off in bulk for use as evidence. BrickHouse Security in New York sells products like this for iPhone and Android. CEO Todd Morris says the handset manufacturers don't support this, so it's a constant effort to keep the forensic software up to date.
"It's a collaboration. There's no way any one company can keep up with Apple or Google," Morris says. "You use programmers from all around the world and they share what they find."
These phone-copying systems rely heavily on what hackers call "exploits," or vulnerabilities in the phones' operating systems that can be used to get around the password or encryption.
Phones locked with a four-digit PIN are usually cracked with what's called a "brute force" attack: The software throws number combinations at the phone until one works, in a way that you couldn't do manually. That can take less than an hour, according to David Dunn.
According to a blog post by Nick Berry, a former rocket scientist and current president of Data Genetics, there are 10,000 possible combinations for a 4-digit PIN using the numbers 0-9. And out of that myriad of possibilities, nearly 11% of all PINs being used are "1234".
The newest iPhones seem to be impervious to cracking and even when police send them to Apple (with a warrant), the extent of the encryption means the company can't always get everything.
"If you use the alphanumeric passcode, even Apple can't get in," says Will Strafach, a hacker who works with companies that make forensic tools for police. He's referring to the longer passwords that are optional on iPhones but also more cumbersome to use.
It's also a slow process. When the newest iPhones are sent to Apple, police may have to wait months for whatever data are recovered, Strafach says.
With Google's Android phones, things are looser. Encryption is optional and the basic screen passcode (or "pattern lock") operates more as a deterrent for the nosy. You can choose longer passwords, but any of them can be circumvented with the user's Google username and password.
With a warrant, the police should be able to get those login credentials from Google.
Sophisticated users are locking things down more effectively. Take the example of Ashkan Soltani, a researcher and computer security consultant.
He uses the basic Android "pattern lock" to open the screen while his phone is in use, but he has modified his phone so that when he shuts it off, it requires a longer pass phrase to boot up again.
"If I'm traveling through customs or being pulled over, I would power off my phone," Soltani says.
"And that PIN would be much longer to access on first boot."
The companies behind the phones have an interest in making them harder to crack, especially when they're marketing to corporate customers. It also reflects the tech world's growing distrust of government.
"At this point, I think it's very difficult to trust any policy-based solution," Moxie Marlinspike says.
That's the pseudonym for a hacker well-known in Silicon Valley for his work on third-party encryption systems for smartphones. He says he cares about legal privacy protections. He says he doesn't want to rely on them.
The oft-abused Third Party Doctrine, it would seem that a warrantless search of a smartphone would be a Fourth Amendment violation. There's just too much information stored on the average smartphone to be compared to anything found on a person during a normal search. And, as a New York law student recently asked Supreme Court Justice Antonin Scalia, isn't searching someone's computer roughly equivalent to their "effects," Fourth Amendment-wise? For all intents and purposes, a smartphone is a portable computer, loaded with a person's "effects" and creating a time/date/location "event" every time it pings a cell tower.
Considering how much info can be gathered from a single smartphone, It's little wonder law enforcement wants to peek at arrestees' smartphones, but the courts need to do a bit of catching up to today's cellphone realities. And there needs to be more attention paid to the fact that law enforcement agencies are partnering with private companies to crack phones, apparently without asking for a warrant first.
http://www.npr.org/blogs/alltechconsidered/2014/03/25/291925559/your-smartphone-is-a-crucial-police-tool-if-they-can-crack-it
http://www.techdirt.com/blog/wireless/articles/20140326/08390126689/police-utilizing-private-companies-exploits-to-access-data-suspects-smartphones.shtml
Don't let personal data escape your smartphone:
Two EPFL researchers have developed an application that automatically secures shared information on a mobile phone. The Android app should be available in late summer 2014.
An EPFL release reports that two EPFL researchers have developed an intelligent application which, once past the beginning machine learning stage, decides for the user what information to transmit or not, and at what level of detail.
http://actu.epfl.ch/news/don-t-let-personal-data-escape-your-smartphone/
The twenty most common PIN password combinations:

Source: http://www.datagenetics.com/blog/september32012/index.html


