The NSA & FBI are spying on Americans through Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple

NSA slides explain the PRISM data-collection program
America, here's hoping you've had enough time to be come to terms with the National Security Agency scooping up all of your metadata pertaining to all of the phone calls you've been making with Verizon, because here comes the next fun news about the government's far-reaching panopticon of total information surveillance, courtesy of Barton Gellman and Laura Poitras of The Washington Post:
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, e-mails, documents and connection logs that enable analysts to track a person’s movements and contacts over time.
The highly classified program, code-named PRISM, has not been disclosed publicly before. Its establishment in 2007 and six years of exponential growth took place beneath the surface of a roiling debate over the boundaries of surveillance and privacy. Even late last year, when critics of the foreign intelligence statute argued for changes, the only members of Congress who know about PRISM were bound by oaths of office to hold their tongues.
The Washington Post obtained "briefing slides" from an "internal presentation on the Silicon Valley operation, intended for senior analysts in the NSA’s Signals Intelligence Directorate," from a "career intelligence officer" who cited "firsthand experience with these systems, and horror at their capabilities," as the reason for the disclosure. These materials described PRISM as "the most prolific contributor to the President's Daily Brief" and the NSA's "leading source of raw material, accounting for nearly 1 in 7 intelligence reports." The Post, goes on to report that while PRISM allows the NSA to collect "anything it likes" from the available data, it is in practice not utilized as a "dragnet" per se:
Analysts who use the system from a Web portal at Fort Meade key in “selectors,” or search terms, that are designed to produce at least 51 percent confidence in a target’s “foreignness.” That is not a very stringent test. Training materials obtained by the Post instruct new analysts to submit accidentally collected U.S. content for a quarterly report, “but it’s nothing to worry about.”
Gellman and Poitras include a detailed history of the PRISM program, along with an explanation of how the system works and the extent to which the technology companies involved offer "resistance" to the data mining, so go read the whole thing.
A section of the PATRIOT Act -- section 215, to be precise -- is what's ultimately guiding the legal affordances here, at least as the Administration is interpreting them. (You may know the section as the "library records" provision, named that way because of the breadth of personal information that can be investigated under its auspices.) Section 215, following the terror attacks of September 11, expanded the powers of the Foreign Intelligence Surveillance Court (the court that, in this case, issued the Verizon order). It established a process, through that court, for compelling businesses to turn over records that may be relevant to the gathering of foreign intelligence or the prevention of international terrorism.
Here's the section language as it currently reads:
The Director of the Federal Bureau of Investigation or a designee of the Director (whose rank shall be no lower than Assistant Special Agent in Charge) may make an application for an order requiring the production of any tangible things (including books, records, papers, documents, and other items) for an investigation to protect against international terrorism or clandestine intelligence activities, provided that such investigation of a United States person is not conducted solely upon the basis of activities protected by the first amendment to the Constitution. ``(2) An investigation conducted under this section shall-- ``(A) be conducted under guidelines approved by the Attorney General under Executive Order 12333 (or a successor order); and ``(B) not be conducted of a United States person solely upon the basis of activities protected by the first amendment to the Constitution of the United States.
`(b) Each application under this section-- ``(1) shall be made to-- ``(A) a judge of the court established by section 103(a); or ``(B) a United States Magistrate Judge under chapter 43 of title 28, United States Code, who is publicly designated by the Chief Justice of the United States to have the power to hear applications and grant orders for the production of tangible things under this section on behalf of a judge of that court; and (2) shall specify that the records concerned are sought for an authorized investigation conducted in accordance with subsection (a)(2) to obtain foreign intelligence information not concerning a United States person or to protect against international terrorism or clandestine intelligence activities.
So am I reading right that it's basically one judge who makes the ultimate decision about the legality of proposed surveillance?
Yes.
And that judge's decision, in turn, would come down to how he or she defines "relevance"?
Sort of. Though we're not (yet?) privy to the original argument the government made to this particular judge, in this particular case, it seems that the logic here is based on the idea that the "tangible evidence" from Verizon is directly relevant to an ongoing investigation -- ostensibly, an investigation into terror threats.
But if that's the argument the government is making, David Cole notes, that's a very, very broad interpretation of the law as it stands. Particularly given the fact that the order involves records of wholly domestic calls.
In other words: it would seem to violate, pretty much any way you look at it, the spirit of the law, if not the letter. As Amy Davidson puts it, "The sophistry lies in pretending that 'metadata' is just about the transaction with Verizon -- the business -- rather than about the privacy of the callers."
http://www.theatlantic.com/technology/archive/2013/06/government-phone-surveillance-for-dummies/276629/
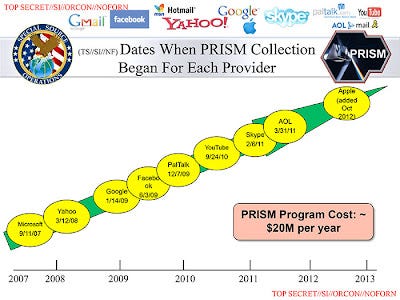
http://www.huffingtonpost.com/2013/06/06/nsa-prism-data-mining_n_3399310.html
Shameless politicians claim the NSA's spying on Americans is classified:
Washington, DC- Senate Intelligence Chair Dianne Feinstein (D-Calif.) said Thursday the National Security Agency program collecting domestic phone records has prevented terrorism. But she and other senators briefed on the program refused to delve into details about how it is used.
Feinstein spoke to reporters after the Intelligence Committee held a "highly classified" briefing on the vast NSA program, which Feinstein said had been put together "quickly" after The Guardian's report on its existence.
Asked whether the program had thwarted any attacks, Feinstein said, "It has, but that's classified."
She added that "there is a report" about how the program has been used, but didn't elaborate.
Sen. Dianne Feinstein: I just had an opportunity to review the Guardian article and I’d like to make the following points.
As far as I know, this is the exact three month renewal of what has been the case for the past seven years. This renewal is carried out by the FISA Court under the business records section of the Patriot Act. Therefore, it is lawful.
Senior officials from the NSA, the FBI, the Office of the Director of National Intelligence and the Department of Justice were all present to explain the surveillance program to 27 senators.
"Members who briefed made comments they were astonished. They didn't know this was happening," Feinstein said.
Feinstein and other senators, however, refused to go into details about what the NSA does with phone records after it has collected them. NBC News reported Thursday that the program extends to every phone call in the country, not just those made through Verizon.
Feinstein said she would not discuss concerns that her fellow senators may have raised during the meeting, because "this took place in a classified briefing, and we don't talk about the substance of it."
Question: One thing that has changed a lot since these letters is there’s a climate that you feel more concerned about civil liberties, the IRS, drone strikes. Is it time to revisit some of the rules and measures you’ve put in place?
Feinstein: Let me put it from my point of view, and then the vice chairman will speak. I read intelligence carefully, and I know that people are trying to get to us. This is the reason why we keep TSA doing what it’s doing. This is the reason why the FBI now has 10,000 people doing intelligence on counterterrorism. This is the reason for the National Counterterrorism Center that’s been set up in the time we’ve been active. It’s to ferret this out before it happens. It’s called protecting America.
The secrecy around such massive surveillance programs has for years spurred critics, including Sen. Ron Wyden (D-Ore.) to ask the NSA to release the secret court orders permitting their use.
He has suggested that it's impossible to have an honest conversation about surveillance programs like the NSA's phone records collection when Americans are in the dark about details.
Speaking after the meeting on Thursday, Wyden seemed frustrated that he wasn't able to discuss the program's specifics. He would not comment on how he thought the NSA's phone records collection could be improved.
"That's thoroughly classified," Wyden said.
http://www.huffingtonpost.com/2013/06/06/dianne-feinstein-nsa_n_3399667.html
http://www.washingtonpost.com/blogs/post-politics/wp/2013/06/06/transcript-dianne-feinstein-saxby-chambliss-explain-defend-nsa-phone-records-program/
Four former NSA analysts warned us about Big Brother spying on Americans:
For years, four former National Security Agency analysts warned that the government was conducting widespread surveillance on domestic communications. Their warnings were largely ignored
After The Guardian newspaper reported that Verizon was turning over customer phone records to the intelligence agency as part of a secret court order, Kirk Wiebe had a “feeling of great gratification.”
“What we've been saying all along has proven to be so," the 68-year-old whistleblower told The Huffington Post. "Our worst fears are being realized.”
While at the NSA, Wiebe, along with Ed Loomis and Bill Binney, created a computer program that could isolate large amounts of information collected by the NSA while protecting Americans’ privacy. But the NSA ignored their program, saying “it was too invasive,” Loomis said.
On Thursday, they had a moment of vindication as they gave interviews criticizing the NSA over a domestic surveillance program they had been warning about.
“This would appear to be the hardcore evidence that I think a lot of people needed to start to believe it,” Binney, who was at the NSA for nearly 40 years, told The Huffington Post. “It’s domestic spying, that’s what it is, on a very large scale.”
NSA whistleblower, Thomas Drake, criticized the court that authorized the surveillance.
“There is no need to call this the Foreign Intelligence Surveillance Court,” Drake said in an interview with Democracy Now on Thursday. “Let’s just call it the surveillance court. It’s no longer about foreign intelligence. It’s simply about harvesting millions and millions and millions of phone call records and beyond.”
“Why do you need to trample on the Constitution for this crazy war on terror?” Loomis said.
http://www.huffingtonpost.com/2013/06/06/nsa-spying-whistleblowers_n_3399258.html


